Over the past week, some users have encountered a known error code with event ID 1091 originating from microsoft-windows-grouppolicy. This problem can arise for several reasons. Now let’s talk about some of them.
Recommended
Windows was unable to register a specific Resultant Set of Policy (RSoP) for Group Policy Proxy% 8. Group Policy settings that were successfully applied to a computer or user in the Marketplace; however, current administrative tools may not report accurately.
In Aria-label = “Article In This Article
How do I check if Group Policy is working in Windows?
In the Command Prompt window, type gpupdate and press Enter. After the main gpupdate command completes, open Event Viewer. Group Policy works correctly if the last Group Policy performance shown in the system game log was one of the following event IDs:
This comment is intended to avoid logging errorsgroup policy when using an unknown field variable.
Applies to: Windows Server 2012 R2
Original Knowledge Base Number: 2003730
Symptoms
What is this message from Group Policy client-side extension?
Message: The security of the Group Policy client extension did not reach the Result Set Attached to the Policy Data Log (RSOP). Please check for any fixable bugs previously reported by this extension. All versions of Windows write unique events to the Application log:
If you are in an Active Directory forest and use a device file security policy, you can view the following logged events:
-
Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2 also logs this event to Group Policy in the activity log:
Protocol name: Microsoft-Windows-GroupPolicy / Operational
Source: Microsoft-Windows-GroupPolicy
Event ID: 7016
Task category: none
Level: Error
Keywords:
User: SYSTEM
Description:
Security extension processing completed in 20984 milliseconds.
XML events:
…
20984
1252
Security
827D319E-6EAC-11D2-A4EA-00C04F79F83A
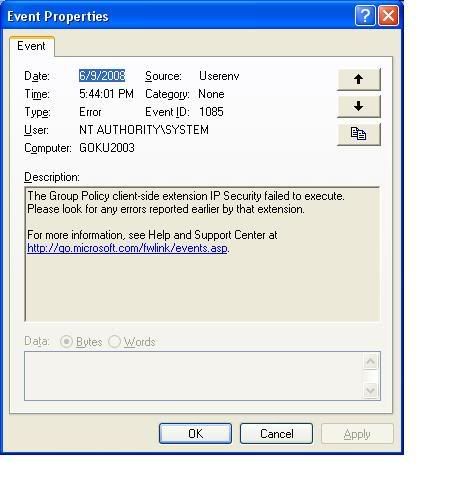
Windows XP and later versions of Windows Server 2003 log this unique event in the application ID: log:
Event 1091
Category: No
Source: Userenv
Type: error
Message: Group Policy Client Security Extension for Resultant Set of Policy (RSOP) data failed. Check for bugs previously reported by this extension.All Windows plans write this event to the application log:
Event ID: 1202
Category: No
Source: SceCli
Type: Warning
Message: Security notices were circulated at the time of the alert. 0xd: Data may not be valid.
Depending on the actual configuration of the policy, there may or may not be new settings in the security policies. The Further Information section explains the terminology for political failure or prosperity (despite errors).
Reason
Events are logged because the file system security settings contain a policy that contains an unknown environment on the computer. To learn more about the issue, enable logging of our own security configuration extension Client side details:
In this% windir% security logs winlogon.log file, you will see one entry like:
Process the GP model gpt0000x.inf.
Error 12: Data is invalid.
Compilation error% PROGRAMFILES (X86)% MyApplication.
% PROGRAMFILES (X86)% is just an example. It is generated when the policy is changed to 64-bit to point to Windows and security settings are made to reach the C: PROGRAM FILES (X86) folder or possibly one of its subfolders.
The gpt0000x.File in the last text file with coverage settings is located in each% windir% security templates Policies folder. This is also the location of the policy in Active Directory on the line that starts with GPOPath, so you can determine which policy has the variable land unknown.
Resolution
To avoid the problem, create another policy at the same level. All are given settings related to the loss environment variable. Then, use a WMI filter to only allow the policy to be applied to machines where the environment variable is set.
Select * after Win32_Envrionment where Name = ‘PROGRAMFILES (X86)’
OptionalAdditional Information
This section explains why policy settings are successfully applied in some circumstances and not in others.
Group Policy Security is controlled by someone’s Userenv.dll running in the Winlogon.exe process or later by the Windows Group Policy Service (GPSvc) in Vista. It is a component that intercepts list policies that are effectively assigned to a machine and filters barely applicable filtering systems. They can be filtered mainly according to mode permissions or WMI filter.
Then Userenv / GPSvc aligns the directives according to their priority. The first policy to apply is the one with the lowest priority, the last one is the highest priority given the Security Directive Client Side Extension (SCECLI) with the policy scope file loaded from SYSVOL.
SCECLI consists of four phases. The first step, which takes the parameters passed to this situation and injects them into the security measures database. In the second step, you request these settings for the whole body, for example, you set the user rights,security styles or set security descriptions for all records and files.
Recommended
Is your PC running slow? Do you have problems starting up Windows? Don't despair! Fortect is the solution for you. This powerful and easy-to-use tool will diagnose and repair your PC, increasing system performance, optimizing memory, and improving security in the process. So don't wait - download Fortect today!

The first phase now lasts until the last policy is identified as being processed. Calling from Userenv / GPSvc to For scecli, the last diagram is a special case. If our call comes in, the first step is still active and the environment for the last directive searches the security database as well as all other directives. But before the nature of the call returns, SCECLI sees that this is almost certainly the final recommendation, and performs a fourth phase within the same call.
Registry file system policy settings are considered costly, SCECLI will likely run them at the point of call in foreground mode. For these settings, Userenv / GPSvc will create a bit more thread so that processing can be completed when the user is already logged in. Domain consoles are an exception to this rule of thumb. You should always follow all of the comprehensive security best practices before an Internet user can log on.
Regarding For missing location variables, SCECLI reads the parameters in the first step and detects an error when resolving the organic variable in the actual path. SCECLI will most likely ignore the entry and continue to add parameters to the security index at a later date. return error in Userenv / GPSVC.
What security policy events are logged in Active Directory?
When a person starts Active Directory and uses a file system security policy, the following events may be logged: Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 log this competition in the policy activity log Group: Security Extension processing completed in 20984 milliseconds.
If the problem occurs in most cases other than the last policy, Userenv / GPSVC will treat the error as a problem with the airport terminal and roll back the security group schema. Therefore, the second stage should not take place. If the problem occurs near the policy, the last SCECLI ignores the specified error and starts the second period. Userenv / GPSVC still violates the application policy due to an error, but in fact the policy management is complete in my step.
- Article
- 4 minutes to read.