Over the past few weeks, some of our readers have encountered a known bug with three types of spyware. Several factors can cause this problem. We will talk about this below.
Recommended
g.There can be several types of spyware, for example, hacker technologies, adware, keyboard recorders, and many others. Each type of malware has its own unique way of working.
There are one or two types of spyware, such as hijacker, adware, keyboard voice recorder and many more. Each type of malware has its own unique way of working.
There are different types of spyware and adware such as browser hijacker, adware, computer keyloggers and many more. Each type of this malware has its own unique way of working.
I have an infected computer, please send error messages by email. Image by patrimonio fit from Fotolia.com
spyware it is a type of platform that can access a mobile computing device without the user’s consent. Other types of spyware have security and data processing implications that can virtually disrupt the functionality of a computer or TV, while other types of software collect content only through templates. To work around this issue, it is helpful to learn about the latest spyware threats and look for signs of infection on your system.
Adware
Adware is a common type of spyware primarily used by advertisers. When you log in, it Records your actual browsing habits to gather additional information about the types of websites users are looking for. This information is indeed used for direct marketing pop-ups and spam.
Voice Recorder
What are the main types of spyware?
Adware. Adware is a very common type of spyware that is primarily used by advertisers.Keyboard recorder. Keyboard Logger Spyware is malware used by hackers.Modem hacker.Browser hijacker.Commercial spyware.
Keyboard Logger is malware, malware used by attackers. This program is designed to dilute personal information by recording the actual keystrokes that you enter on your laptop. When you enter a PIN, security code, or credit card number, the key recorder records them for zeros. This information can be used to attribute attempts to access the system, as well as to commit identity theft and fraud.
Modem Hacker
Modem hackers inject unauthorized calls into your phone and access the participants’ world wide web through your online connection. Usually this excellent spyware is designed to get premium cell phone numbers and connect to websites like porn membership sites. You will notKnow about internet access and calling until you see my unauthorized payments on your account.
Browser Hijackers
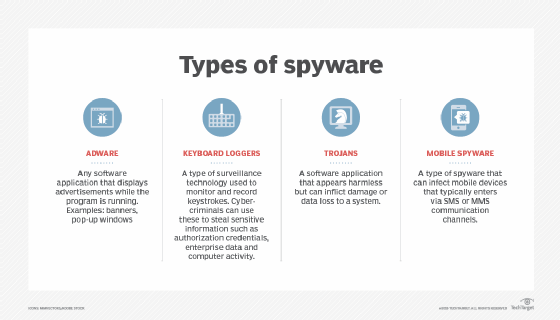
Browser spy hijackers affect your personal Internet access by dropping your page and bookmarks. It is a target that will direct you to unwanted websites through commercial spam. These programs are also data miners that log savings in your browser and sell information to advertisers.
Commercial Spyware
What are the 4 types of spyware?
Spyware is mainly divided into four types: adware, system tracking, tracking including web tracking, and Trojans. … … Examples of other notorious types include online digital rights management, home phone features, keyloggers, rootkits, and web beacons.
Not all spyware is tracked. In some cases, companies that provide you with free software and social media apps will ask you to consent to spyware scans to gain access to their systems. They then send you targeted laser advertisements when you use their system. In this case, you partially use your privacy to gain access to free software.
Scott Yoder is a professional SEO copywriter and copywriter specializing in content creation.Your online marketing content. He graduated from the University of Oregon with a BA in English. A former mentor and curriculum writer for public education, he now writes mainly on online marketing, environmental business, progress, legal and medical topics.
What are the top 3 malwares?
Ransomware. Ransomware is application software that uses encryption to completely disable a target’s data access for a ransom payment.Malware without a file.Spyware.Adware.Trojans.TO.Virus.Rootkits.
In this article, we discuss what adware is, the most common types of adware, and how you can protect yourself, your employees, and your data beyond spyware.
What Spyware?
What is spyware and its types?
Spyware related types Spyware is not only a software type. This is a whole category of malware, which includes adware, keyboard recorders, Trojans, and programs to steal information from mobile devices.
Spyware is toxic software that continuously monitors your computer’s activity and Internet targets. Its purpose is to capture a concept often referred to as personal traffic data, which can include keystrokes, screenshots, visited online stores, or various types of personalized or confidential information. The data can also be used in many ways, including for sale to interested companies or, in some cases, for identity theft. Very importantunderstand these types of known spyware and understand how to detect them.
The plan can be infected with spyware, just like this task is infected with other types of malware, including Trojans, viruses, worms, etc. You can take advantage of various security features, for example, when a user clicks on an unknown connection in an email , or simply checks for a malicious website. Users will certainly be happy to download them when they are used as all sorts of useful applications or as freeware.
Why Is Spyware So Important?
Since phishing attempts are better researched every day, it is very important that your employees are well trained in how to prevent and learn how to prevent phishing attacks. We’ve seen that threat protection companies are still confusing various phishing attempts as these products become more difficult to detect. More recently, the CEO of a large company fell victim to a phishing attempt and was forced to sell hundreds of thousands of profits to rebuildupload your data. People come first and build this past defenses, so it is very important to educate staff on how to avoid this.
How To Determine If Your Computer Is Infected With Spyware
The best way to detect this plethora of software is to install a modern firewall, antivirus, or antivirus program on your device. They can alert you if your computer routinely experiences suspicious activity or additional security threats.
There are other telltale signs that indicate what spyware and adware has been injected into the system. They rarely run on their own on your company’s computer, which means your device has indeed been infected multiple times. Sometimes users experience significant system performance degradation such as high CPU activity, CD / DVD usage, or unexplained network traffic.
Various apps and applications may intermittently or potentially experience crashes, freezes, process startup errors, or even problems connecting toThe Internet. Certain types of spyware can disable firewall and antivirus in addition to other browser protection settings, greatly increasing the risk of future infections. If everyone encounters any of these issues, it is likely that your system has been infected with spyware or other malware.
What Are The Most Common Types Of Spyware?
Usually the functionality of a particular spyware is the intent of its author. Here are four examples of the most common types of spyware.
Keyloggers – also known as system monitors, keyloggers appear to be designed to record the actions of these computers, including keystrokes, search history, email activity, room communication, chat, connected websites, system credentials, etc. e. Sophisticated whiteboards can also collect documents that come straight from printers.
Recommended
Is your PC running slow? Do you have problems starting up Windows? Don't despair! Fortect is the solution for you. This powerful and easy-to-use tool will diagnose and repair your PC, increasing system performance, optimizing memory, and improving security in the process. So don't wait - download Fortect today!

Stealing password. As the name suggests, spyware necessarily collects passwords entered on an infected device. This can include issues such as login credentials andwhether handling these important passwords.
Infostealer: When a computer or other device containing spyware is infected, it can provide third parties with sensitive information such as passwords, usernames, email addresses, files, report, browsing history, system information, Excel spreadsheets , documents, media files, etc. As a rule, Infostealer exploits security holes in browsers that collect personal data and other informational information.
What are the 4 types of spyware?
Spyware is mainly divided into four types: adware, system monitors, tracking, including advanced tracking on the Internet, and Trojans; Examples of all other notorious types are digital correct administrative functions that “call home,” keyloggers, rootkits, and web beacons.
Banking Trojans. Similar to theft, info-finance Trojans exploit browser security holes and obtain credentials from financial institutions, convert content from transactions or websites, or insert additional transactions, including web finance portals, digital brokers, wallets, and more. financial funds can fall prey to these Trojans.
Conclusion
The digital environment is fraught with organic risks, as does the dilemma of spyware or other layers of malware. Fortunately, there are several tools to help you, and in the future.Then your business will be protected from online threats from these people.

What is the most common type of spyware?
Keylogger: This is one of the most fake types. A keylogger records keystrokes on a person’s computer. The most beneficial risk is that passwords can usually also be saved as you enter them, for example when buying a credit card to make a new purchase. Adware: This is the most common new type.
What are the names of spyware?
XNSPY. With this application, you can remotely and remotely manage some of the works on the device.FlexiSpy. FlexiSpy is considered a great choice for co-managing multiple devices, downloading phone calls to a car, and tracking some calls.Spyzie.SpyEra.
What are the types of spyware?
Adware, pornographic and dangerous software includes legally developed software that, under certain circumstances, may be used as specific threats to assist computer users (including spyware).
What are the 4 types of spyware?
Spyware is mainly divided into four types: adware, system monitors, tracking including web trackers, and Trojans; Examples of several other notorious types are digital rights management functions that “soundnyat home ”, keyloggers, rootkits and therefore web beacons.
What are the top 3 malware types?
The most common types associated with malware are viruses, keyloggers, worms, Trojans, ransomware / crypto-malware, logic bombs, bots / botnets, malware and spyware, and rootkits.
Drie Soorten Spyware
Trzy Rodzaje Oprogramowania Szpiegujacego
Tres Tipos De Software Espia
세 종류의 스파이웨어
Tre Tipi Di Spyware
Trois Types De Logiciels Espions
Tres Tipos De Spyware
Drei Arten Von Spyware
Tre Typer Av Spionprogram