You may receive an error message indicating how to interpret the Linux kernel dump file. There are several steps you can take to resolve this issue, and we will do so shortly.
Recommended
How to open the core dump file in Linux?
$ gcc -g -o items something.c $ ./something segmentation error (core dumped) money gdb something core You can get this for posthumous debugging. Some gdb: br commands output the package, fr go to the given stack structure (see the output of the br command).
# nanoSegmentation fault
# nanoLack of segmentation (core lsCore
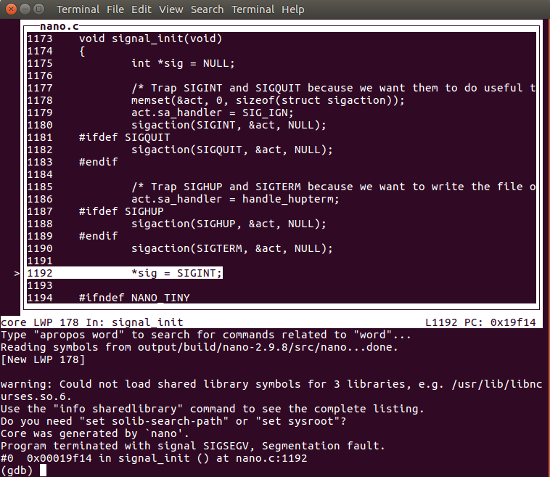
$ exit)# arm-linux-gdb -l core-nanoThe core was created on the basis of "nano".Program terminated with SIGSEGV, segmentation fault.# 0 0x00019f14 in signal_init () on nano.c: 11921192 * sig = SIGINT;
$ arm-linux-gdb -c interior -tui
(gdb) nano-print signal$ 1 implies (int *) 0x0(gdb) bt# 0 0x00019f14 via signal_init () to nano.c: 1192# 1 0x0001b264 relative to main (argc = 1, argv = 0xbee9de64), probably at nano.c: 2568
- GDB can be used to search for the disability string mentioned earlier in the section: How to choose program kernel development. When does a GDB file have what command line parameters?
- main file contains CLI user arguments, they do not need to be strikethrough again
-
objdump -s corecan be used randomly to save a lot of memory.
#include #include #include #include myfunc interval (i interval) * (int *) (NULL) matches i; / * Line 7 * / return i and 1;int main (int argc, char ** argv) / * Configure callback. * / char data_ptr [] implies "String in segment"; bandwidth char * mmap_ptr; char * text_ptr = "String in the whole text segment"; (empty) argv; mmap_ptr means (char *) malloc (sizeof (data_ptr) + 1); strcpy (mmap_ptr, data_ptr); mmap_ptr [10] matches 'm'; mmap_ptr [11] matches 'm'; mmap_ptr [12] implies 'a'; mmap_ptr [13] matches 'p'; printf ("text address:% p n", text_ptr); printf ("data address:% p n", data_ptr); printf ("mmap address:% p n", mmap_ptr); / * Call execution to prepare the stack trace. * / return myfunc (argc);
gcc -ggdb3 -std = c99 -Wall -Wextra -pedantic -o main.out main.culimit -c unlimitedrm -f kernel./ Main output
How do I analyze a crash dump file in Linux?
Install the Kdump tools. First install kdump which is part of the kexec-tools package.Place the crash kernel in grub. Conf.Configure the location of the dump.Set up the main manifold.Restart kdump services.Manually run a core dump.Look core files.Kdump analysis with crash.
Text address: Address: 0x4007d4Data 0x7ffec6739220mmap address: 0x1612010Segmentation fault (unloaded kernel)
How do I read a core dump file?
While walking, press Ctrl + to bring up the actual core dump. You will now see the base file in the directory you are in. Since we don’t have the debug symbols executable to support this, our command just opens the underlying data in gdb instead of the symbols executable + base file.
GDB tells us the exact line by which the segmentation was performed, which is what most people need to debug today:
gdb -q -nh main.out core
Read main.out symbols ... done.[New LWP 27479]The kernel was generated by `./main.out '.The program was interrupted by signal SIGSEGV, segmentation fault.# 0 0x0000000000400635 for myfunc (i = 1) on main.c: 77 * (integer *) (NULL) I;(gdb) matches bt# 0 0x0000000000400635 in myfunc (i = 1) found on main.c: 7# 1 most important 0x000000000040072b (argc = 1, argv = 0x7ffec6739328) on main.c: 28
CLI arguments are often stored in the main file and do not need to be reused
To address specific issues related to CLI arguments, we will see that if we start CLI arguments like:
rm -f core./main.out 1 2
then this will be reflected in the previous version of Bactrace without changing our commands:
token read from main.out ... done.[New LWP 21838]The kernel was started with `./main.out 1 2 '.Aborting the program using the SIGSEGV signal, segmentation fault.# 0 0x0000564583cf2759 in myfunc (i = 3) on main.c: 77 * (int *) (NULL) matches i; / * Line 7 * /(gdb) bt# 0 At 0x0000564583cf2759 myfunc (i = 3) is available on main.c: 7# 1 0x0000564583cf2858 in main (argc = 3, argv = 0x7ffcca4effa8) with main.c: 2
Notice how correct argc = 3 is. Hence, this should mean thatthis information is stored throughout the main file. I suspect it only stores it for the main arguments, only those arguments that are stored from another function.
This makes sense regardless of whether the kernel dump is to persistently save all memory and then save program state, and so it has all the suggestions needed to immediately determine the value of a function’s arguments on the stack.
How to examine an environment variable is less obvious: how to get a ground variable from a kernel dump Environment variables are also in internal memory, so objdump contains this special information, but I don’t know which way I’m to list them all at once when it comes before using one at a time, like this, but I was working on these tests:
p __about [0]
Using Binutils systems such as readelf and objdump we will probably bulk feed information to core – Included file like the ability to remember the state.
Most / everything should also be visible through GDB. These honest Binutils tools areThey provide a richer methodology that is useful for specific implementation cases, while GDB is more convenient for more interactive exploration.
core file
tells you and me that the core file is usually an ELF file:
core: 64-bit base ELF x86-64 LSB, version specific only (SYSV), SVR4 style, from './main.out'
This way, we can investigate the problem more directly with the usual Binutils tools.
A quick look at the plant’s ELF keg reveals that there is indeed a specific type of ELF designed for it:
Elf32_Ehd.e_type == ET_CORE
How do I decode a core file?
If you are trying to play the main music file, make sure it is on the operating system it was originally provided with. Copy the main file to a location like this if it doesn’t already exist:interrupt function [file:]. Set a breakpoint at the function level (in the file).commit [fraud]bt.Printagainst.Next.Edit the [File:] function.
Mann Core
readelf 5 -Wa core
Recommended
Is your PC running slow? Do you have problems starting up Windows? Don't despair! Fortect is the solution for you. This powerful and easy-to-use tool will diagnose and repair your PC, increasing system performance, optimizing memory, and improving security in the process. So don't wait - download Fortect today!

gives some advice on file structure. It seems that memory is contained in many program headers:
program header: Type Offset VirtAddr PhysAddr FileSiz MemSiz Flg Align NOTE 0x000468 0x0000000000000000 0x0000000000000000 0x000b9c 0x000000 0 LOAD 0x002000 0x0000000000400000 0x0000000000000000 0x001000 0x001000 R E 0x1000 LOAD 0x003000 0x0000000000600000 0x0000000000000000 0x001000 0x001000 R 0x1000 LOAD 0x004000 0x0000000000601000 0x0000000000000000 0x001000 0x001000 RW 0x1000
and in Some note areas should contain additional metadata, in particular prstatus , that the PC contains:
How to analyze a program’s core dump file with GDB?
g.The core dump log for the “process” is generated as the actual “core.pid” file. After entering the GDB prompt (while running the above command) enter: (gdb) where this will probably give you information for that stack where you can analyze the cause of the crash / crash.
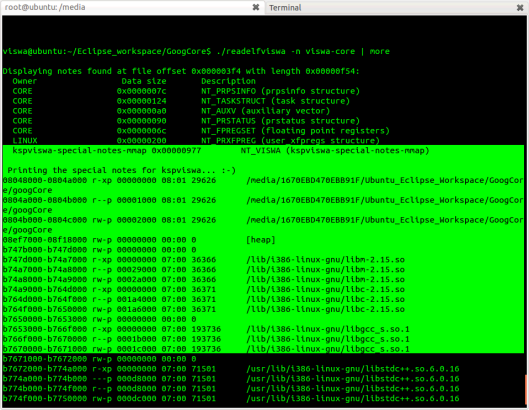
Show notes found in file reduced from 0x00000468 to length 0x00000b9c: Description of the owner data form CORE 0x00000150 NT_PRSTATUS (prstatus structure) CORE 0x00000088 NT_PRPSINFO (prpsinfo structure) CORE 0x00000080 NT_SIGINFO (siginfo_t data) CORE 0x00000130 NT_AUXV (auxiliary vector) CORE 0x00000246 NT_FILE (affected files) Page size: 4096 Offset from start to end 0x0000000000400000 0x0000000000401000 0x0000000000000000 /home/ciro/test/main.out 0x0000000000600000 0x0000000000601000 0x0000000000000000 /home/ciro/test/main.out 0x0000000000601000 0x0000000000602000 0x000000000000001 /home/ciro/test/main.out 0x00007f8d939ee000 0x00007f8d93bae000 0x0000000000000000 /lib/x86_64-linux-gnu/libc-2.23.so 0x00007f8d93bae000 0x00007f8d93dae000 0x00000000000001c0 /lib/x86_64-linux-gnu/libc-2.23.so 0x00007f8d93dae000 0x00007f8d93db2000 0x00000000000001c0 /lib/x86_64-linux-gnu/libc-2.23.so 0x00007f8d93db2000 0x00007f8d93db4000 0x00000000000001c4 /lib/x86_64-linux-gnu/libc-2.23.so 0x00007f8d93db8000 0x00007f8d93dde000 0x0000000000000000 /lib/x86_64-linux-gnu/ld-2.23.so 0x00007f8d93fdd000 0x00007f8d93fde000 0x00000000000000025 /lib/x86_64-linux-gnu/ld-2.23.so 0x00007f8d93fde000 0x00007f8d93fdf000 0x0000000000000026 /lib/x86_64-linux-gnu/ld-2.23.so CORE 0x00000200 NT_FPREGSET (floating point register) LINUX 0x00000340 NT_X86_XSTATE (extended s Distance x86 XSAVE)
objdump -s core
Content of the load1 zone: 4007d0 01000200 73747269 6e672069 6e207465 .... Te string 4007e0 78742073 65676d65 6e740074 65787420 xt segment. TextLoad15 content section: 7ffec6739220 73747269 6e672069 6e206461 74612073 String of characters in important information s 7ffec6739230 65676d65 6e740000 00a8677b 9c6778cd Example .... g {.gx.Contents of the load4 section: 1612010 73747269 6e672069 6e206d6d 61702073 guitar string in mmap s 1612020 65676d65 6e740000 11040000 00000000 Element ..........
This has been tried and tested on Ubuntu 16.04 amd64, GCC 6.4.0 and binutils 2.26.1.
Speed up your PC today with this easy-to-use download.How do I read a core dump file?
Press Ctrl + at runtime if you need to force a core dump. You will already see the main file in our propertythe directory you are in. Since people all over the world don’t have an executable for this awesome one with debug symbols, now let’s open an important file in gdb instead of any executable with symbols + actual base file.
How do I decode a core file?
If you are trying to read the main file, make sure it is on the same operating system that it was created on. Copy the master data file to this location if it doesn’t already exist:Interrupt function [apply:]. Set the actual breakpoint for the function (in the file).commit [fraud]bt.Printagainst.Next.Edit the [File:] function.
How do I analyze a crash dump file in Linux?
Install the Kdump tools. First, post kdump, which is partially related to the kexec-tools package.Determine the failure of the grub kernel. Conf.Configure the location of the dump.Set up the primary header.Restart kdump services.Manually run a core dump.Take a look at the core files.Kdump analysis with crash.
How do I read a core file in Unix?
At the UNIX command line, enter the following command line: dbx-program-name kernel-name.Examine all the call payload in the main file. You can always get information on how to do this by running man dbx from the UNIX command line.To exit this dbx command, enter quit at the dbx command line.
How do I read a core dump file?
While this window is running, press Ctrl + to enter Cause heart loss. You will now see the main content in the directory you came from. Since we do not have an executable with debug symbols for this, we simply open the main file in the GDB consumer of the executable with drawings + main file.



