Recommended
Today’s blog post is designed to help you if you receive a spyware registry file error code.
:
Registration
Summary Malware can crash any Windows operating system and all data on that particular device. In order toTo keep their computer safe, anyone can use third-party antivirus software to scan and remove malware. However, this is another way to remove malware from the Windows registry. MiniTool Will will show you how to use the second method for this job.
Let’s talk about you, the Windows Registry … yes, this cryptic and therefore dangerous part of the operating window structure that warned us just when we were about to screw up our first computer. Turns out the Windows Registry isn’t as scary as everyone claims it will be. However, if you do not know what you are doing right, there are many opportunities to seriously spoil the installed package and the operating system itself. But not only is this really easy to fix (back up, back up, back up!), You also have to be pretty careless about what changes you seem to have made.
When I let go of my preconceptions about the Windows Registry, I realized how powerful it can be. Of course, attackers alsothey are not aware of special power. Like other information management and processing tools, the Windows registry can be used for its intended purpose or for questionable purposes. Since it is embedded in the operating system, it is a new primary target for attacks and attempts to circumvent standard security measures. With that in mind, I’m going to introduce you to some of the common attack vectors associated with tactics that use the Windows Registry.
Tactic 8: Using the Key Log for Spyware Attacks
As mentioned earlier, the Windows Registry is the central part of Windows and contains a lot of raw data. This data could very soon be used against you by this attacker or data mining software. An example would be a small registry query to see if any Remote Access Tools (RAT) like TeamViewer, VNC, or pretty much Terminal Services are connected. With this information, any attacker can distribute and redistribute these accessories throughout the home, or find their way to very high prices And interesting systems.
An increasingly common tactic is to use registry keys to directly store and hide code for the next step in protecting malware after it has been placed on the system. What is a Windows Registry Key? A registry key is considered an organizational unit in each of our Windows registries, just like a folder.
Also, the malware undoubtedly uses Windows native tools when it comes to execution commands, so it simply cannot be detected by signature-based security software such as antivirus.
Here’s An Example Of Behavior …
First of all, the end user got an Adobe Fake Flash update popup even though they were running from a different domain via Firefox:
Shortly thereafter, JavaScript code was downloaded that tried to disguise itself as a Firefox fix:
It is then executed through the instantiated Windows native script wrapper wscript.exe :
How do I find malware in my registry?
Click on the “Start” button to which “Run” points. This opens the nominal menu window. Enter “regedit” and click “OK”. This will open the Microsoft Windows Registry. Open the “HEKY_LOCAL_MACHINE” folder, which will help you scan your registry for viruses. Usually this is where the main virus enters the system.
When executed, this JavaScript presented a command prompt window to close the user and showTo him that a great “update” is already in progress and in progress. While this topic was being discussed, an external network web connection was established to the malicious domain, and further instructions were followed to write commands to a registry key on that system.
Now that you have begun the next steps to write to this registry key, a great example of the built-in Windows gizmo mshta.exe is to place the marketer in a registry key in a large Windows script shell. moved to. This will write a specific command to a flexible environment on the infected host.
A similar process cmd.exe then starts PowerShell, which recommends the Invoke-Expression cmdlet, a common concurrency that we’ve seen and explored in previous feature discoveries.
Finally, one or more subprocesses are created, associated with either regsvr32.exe or rundll32.exe . Next, we often see hundreds, if not thousands, of external network connections established with ad domains to select the revenue generated from ad clicks.
Finally, but not usually, a storage mechanism is introduced. ia:
Tactic 2: Run Windows Keys And Startup Folder In Permanent Mode
How do I find malware in my registry?
Once a subject or malware reaches an endpoint, it is usually ensured that resources can continue to be used through persistence mechanisms. Most of us in the field are familiar with the startup key and using the Windows startup folder to create persistence on the mining endpoint, but this tactic has certainly not gone anywhere, so it is definitely worth talking about and, along the way, save the reviews to mind.
Usually the easiest tactic is to use the Windows Startup folder at:
C: Users . The associated shortcuts (.lnk extension) in this directory means that Windows launches the shared application every time logs on to Windows. It is believed to be used by various forms of adware, but it can also be easily identified and fixed by simply removing the shortcut.
Recommended
Is your PC running slow? Do you have problems starting up Windows? Don't despair! Fortect is the solution for you. This powerful and easy-to-use tool will diagnose and repair your PC, increasing system performance, optimizing memory, and improving security in the process. So don't wait - download Fortect today!

The execution keys in your computer’s Windows registry do the same, but they canStay in several different places:
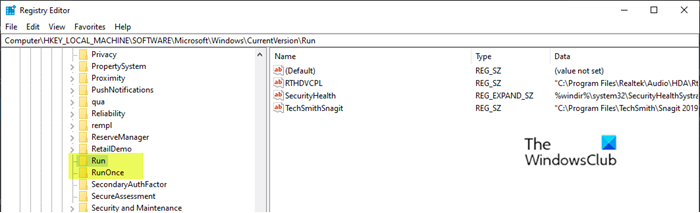
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion Run
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion Run
- HKEY_LOCAL_MACHINE Software Microsoft Windows CurrentVersion RunOnce
- HKEY_CURRENT_USER Software Microsoft Windows CurrentVersion RunOnce
Are registry files safe?
The difference between HKEY_LOCAL_MACHINE and therefore HKEY_CURRENT_USER is whether the specified exe is run on startup for a specific login worker or customer (the current_user is copied to the compound “user hive” and loaded whenever the user can login). Then there is Run and RunOnce ; the only difference is that RunOnce immediately deletes the entry if it is working profitably.
When this persistence method is received, the malware continues to exchange to ensure that the advertising web directories are affected (in cases where the malware just clicks), rogue commands and wow control areas are beacons (in cases like bot- networks where more commands are needed to actually send to infected machines) and / or perhaps constantly trying to coerce the end user The owner will often refer to the van’s pop-up links for any click for numbers related purposes.
Tactic 3: Exploit Weaknesses In Service Registry Permissions To Achieve Persistence
Another way to establish persistence, which also helps maintain elevated privileges, is to change the settings for the services that start each time Windows starts. If the permissions are not well configured (think of the principle of least privilege), while the registry keys can be changed for pleasant maintenance, the ImagePath or binPath key can be configured to target a malicious binary or a new one. Instead, a link to the generated file. It is possible not only to run malware on Windows startup, but also to run under the balance of the local system with elevated rights. Keep in mind that this behavior is common in many software installers and can be a tool for false positives when checking for changes. However, this is still a great and destructive place for software to be forgotten.heels your high-heeled sandals to your end points. All software clocks should be checked whenever changes are made to this part of the registry.
What You Can Do To Protect Yourself
How do I remove malware from my registry?
Now that you understand or know what these types of registry window attacks look like, what can you do about them? Consider practical steps to strengthen your defenses. One of the best ways to defend against registry window attacks is to whitelist the software or comply with the local group’s insurance restrictions. This way, you can be sure that you are in control of all our applications and permission levels. Remember forever that whitelisting is not a panacea and can always be bypassed, as we explored in our article on How to Bypass Application Whitelisting. If your culture does not allow it, the next step is to use a rampaging monitoring agent to detect changes to these registry keys or to the original entry.
First of all, remember that understanding is power. Don’t be afraid of the Windows Registry; Find out what the following know it’s not how He’s a super-secret holy grail guy tied to a ship that no one can feel. Attackers are already using it around you, so you need to know this and know what should and should not be normal. The better you know your operations corps, the better armed you are to understand and defend against attackers.
Can registry key malware?
Many layers of malware also tweak the registry to automatically install and disable security tools. The latter is often a case of simple baud rate changes that can be reactivated without noticeable difficulty.
Are registry files safe?
Why REG files can be dangerous If you get the .reg file for a good reason and there are no errors, that’s okay. For example, anyone can write their own REG statement to quickly make their favorite fixes on any new Windows PC. It can mess up various configurations or delete parts of a specific type of Windows registry on startup.
How do I find malware in my registry?
Click some of the Start buttons and then click Run. This will open a small menu window. Enter “regedit” and click “OK”. This will open the Microsoft Windows Registry. Open the HEKY_LOCAL_MACHINE folder to check the registry for viruses. This usually happens when a virus is installed on the system.
Can registry key malware?
Many types of spyware and adware also modify the registry, each of which installs and removes security tools. The latter is often the case when the edit contains simple binary values that can be continuously reactivated without much difficulty.
Are registry files safe?
Why REG files can be dangerous If the REG file is from a trusted source and is free of errors, it is huge. For example, you can write this custom REG file to quickly make changes to it on any new Windows PC. It can mess up various settings or delete parts of the Windows registry while it is running.
Fajly Reestra Shpionskih Programm
Arquivos De Registro De Spyware
Spyware Registerbestanden
Archivos De Registro De Spyware
Spionprograms Registerfiler
Fichiers De Registre De Logiciels Espions
File Di Registro Dello Spyware
Spyware Registrierungsdateien
Pliki Rejestru Programow Szpiegujacych
스파이웨어 레지스트리 파일